NSX-T Series: Part 8 – Logical Switching Use Cases
In this “NSX-T Series: Part 8 – Logical Switching Use Cases” part, we will discuss the steps to configure logical switching for NSX-T Data Center. We will go through the service involved in switching and will try to find out the benefits of SDN Model with its use cases.
But if you want to start from the beginning you can refer my previous part of this Series:
Architecture and Deploy
Adding Compute Manager
Planning NSX VXLAN
Transport Zones and Use cases for Multi-Transport Zone
N-VDS and VDS 7.0
Uplink Profile
NSX-T ESXi Transport Node
Challenges in Traditional Networking and Solution with NSX-T
1. Large layer 2 network
Challenge:
Layer 2 network is the base for any switches and the protocol which we have been using is Spanning Tree Protocol. It has his own benefits but as network is changing drastically the tree topology is not feasible, for any data center where we are investing a lot for the link and circuits.
We have witnessed many nasty scenarios where the L2 loops brings down the complete environment, which is not at all good in Data Center. As well this model ask a lot from Core switches as per it’s capability.
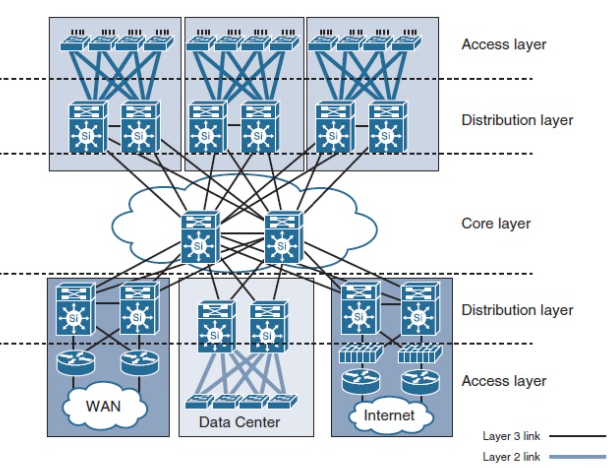
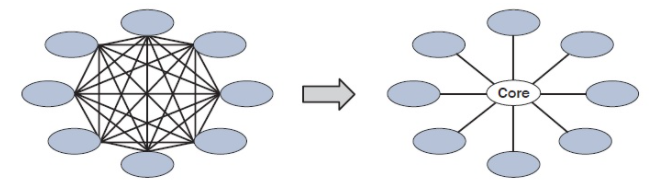
Solution:
To contain the L2 network domain less VMware demands to have smaller domain so that it can basically runs it’s base services( Esxi Mgmt, VSAN, NFS and vMotion). But when it comes to VM data plane it can span over VXLAN Network and do not demand to create VLAN per L2 segment, this is one the major benefit of using VXLAN. Though even to contain VMware base traffic many design also go through NSX over ACI, NSX over BGP-EVPN model ( etc).
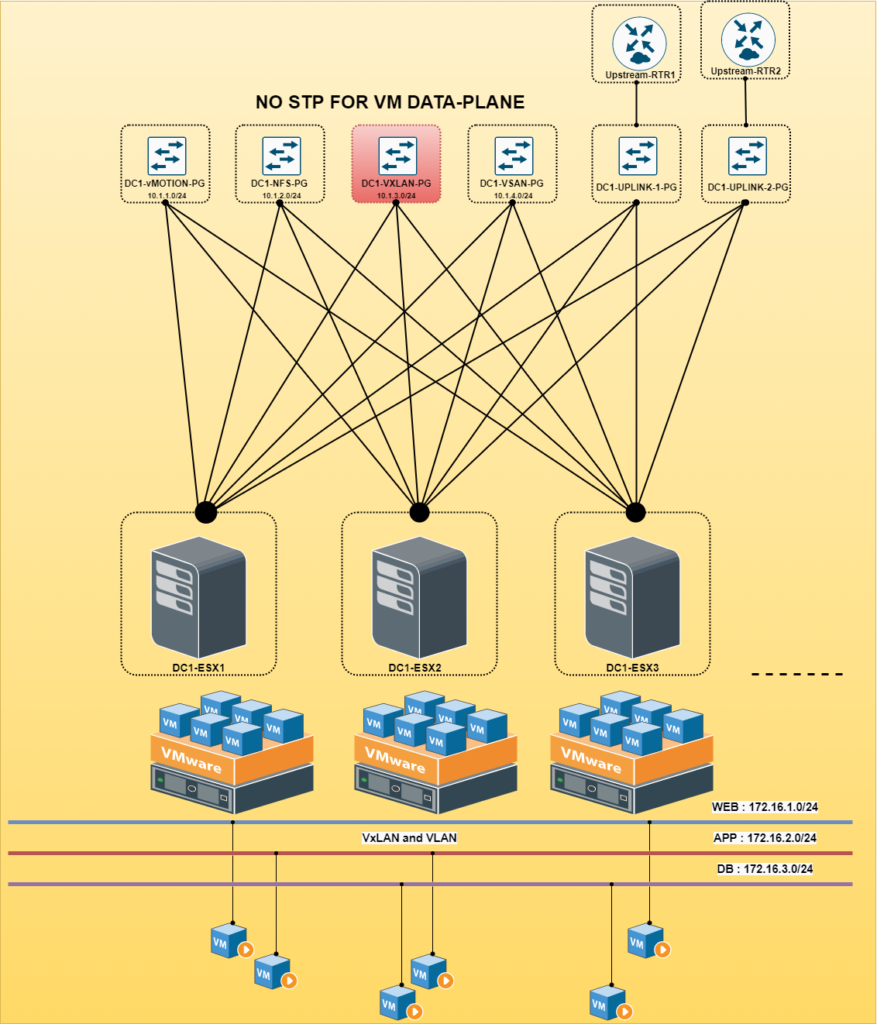
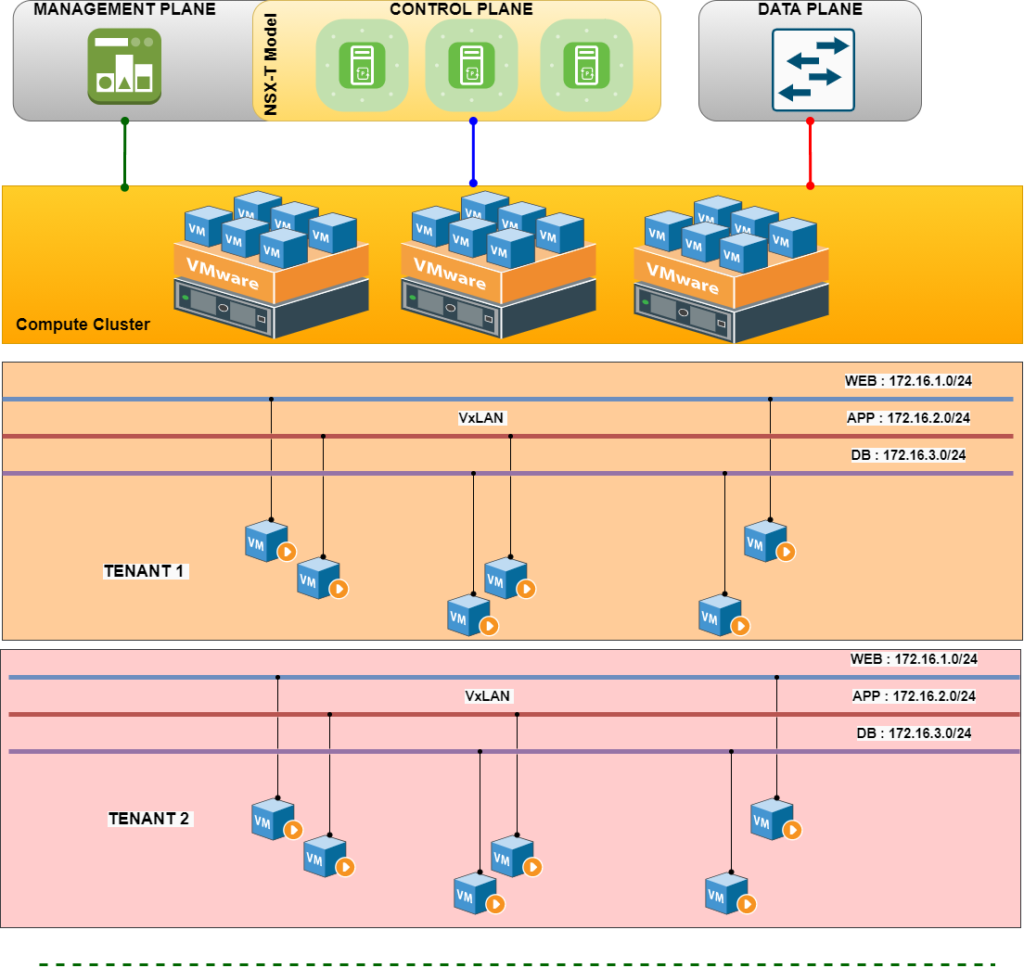
2. Multi-Tenancy ( Customer basis or Application basis )
Challenge:
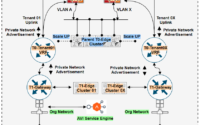
Achieving multi-tenancy is always a best project for any Network engineer, but traditionally it had many complexity. Though achieving multi-tenancy we have 2 base option : VLAN on L2 and L3 VRF on L3. Different vendors ( Fortinet-VDOM, Palo Alto-vSYS or VRF, etc) refer with different name but base is either VLAN or VRF. And as the number of demand increase we can across with the exhaustion. In below diagram it represent physical and logical segmentation of a common environment. Even this model demands to have high end capacity of MAC and FIB.
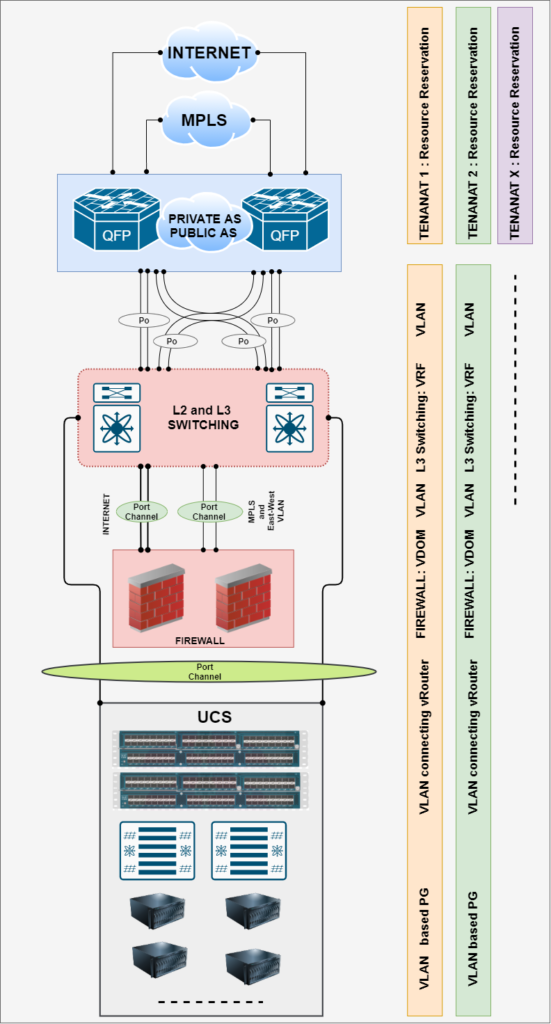
Solution:
Spanning the workload via overlay technology is one the suited solutions which could be via VXLAN, NVGRE, etc. This gives the scalability pretty as compared to VLAN and VRF. And deploying it with SDN model gives you benefits of not following traditional method of flooding, and gives a lot benefits in terms of MAC/FIB limits if we have in any environment. ( Though VXLAN can be deployed via Flood and Learn model – which is kind of less used, BGP-EVPN – need to have extensive knowledge on BGP )
Though there can be a separate detail blog on the benefits but let’s keep short as this is moreover the basic benefits.
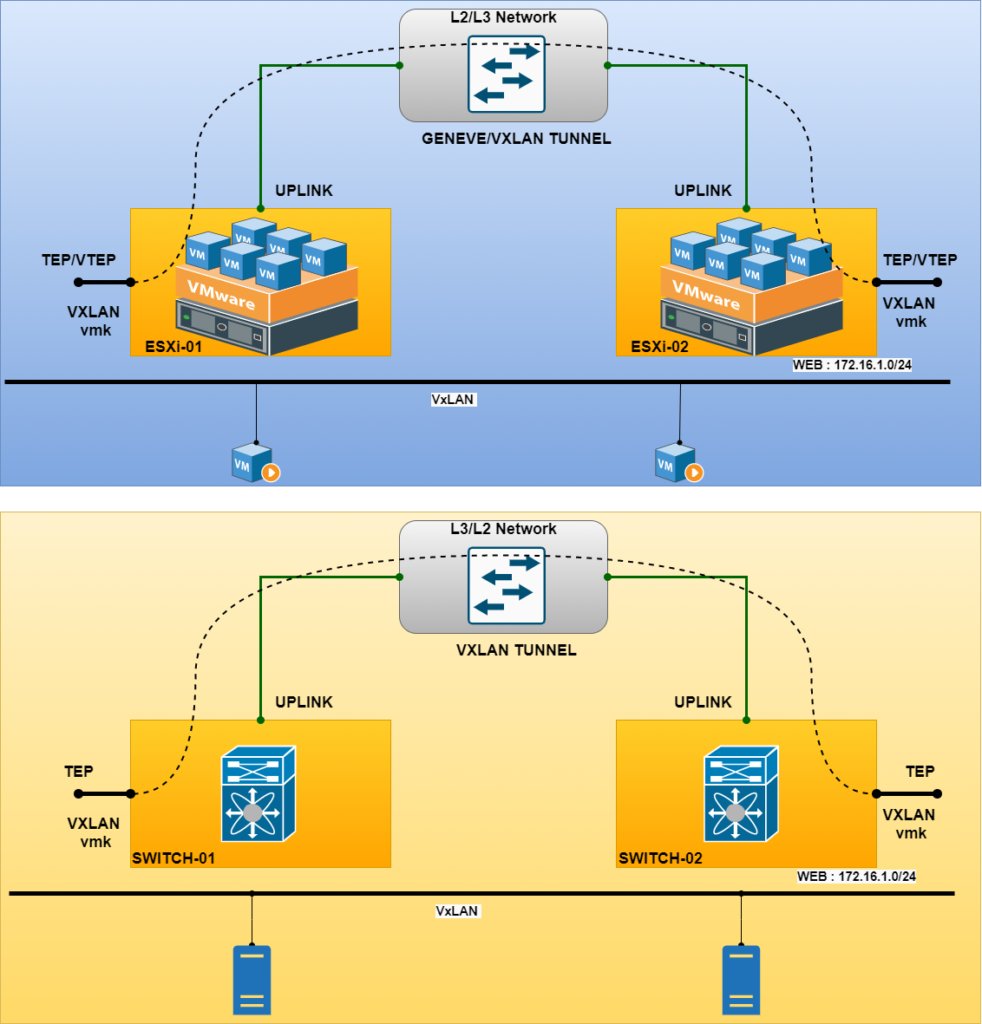
What is tunneling
Tunneling encapsulates the network traffic and carries it over any network, and the encapsulation is taken care of by TEP ( Tunnel End Point). For detailed information on this please refer to my previous blog Planning NSX VXLAN.
NSX-T uses Geneve to encapsulates the data traffic, which at backend is VXLAN only which in other work is customized VXLAN from VMware. Earlier we have seen this from Cisco with their Cisco ACI, they also uses customized VXLAN.
Geneve is an IETF overlay tunneling mechanism providing L2 over L3 encapsulation of data plane packets.
Geneve-encapsulated packets are communicated in the following ways: 1.The source TEP encapsulates the VM’s layer 2 frame in the Geneve header. 2.The encapsulated UDP packet is transmitted to the destination TEP over port 6081.
3.The destination TEP decapsulates the Geneve header and delivers the source frame to the destination VM.
How to configure Logical Switch/Logical-Segment/VXLAN-PG in NSX-T
Configuring logical-segment in NSX-T the pre-requisite should be followed which we discussed in previous blogs. To deploy logical-switch one need to go Network>> Segments option.
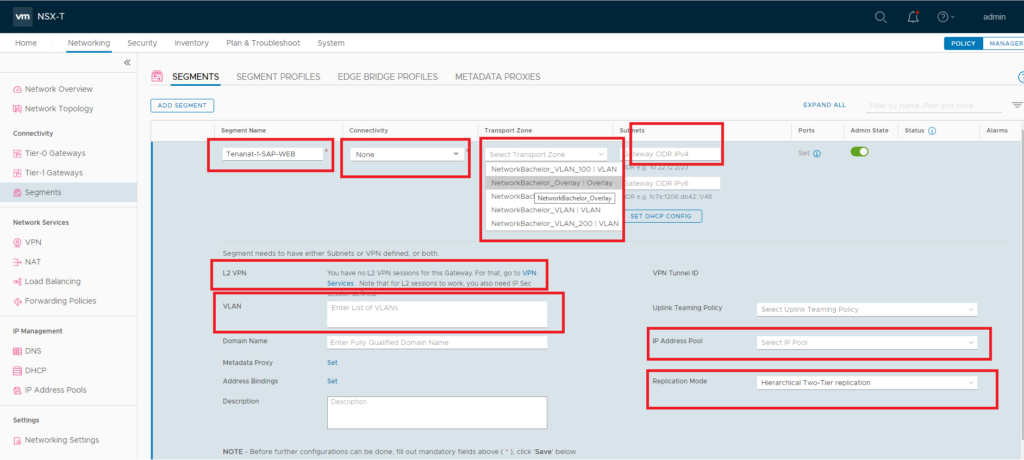
While adding VXLAN you have many options :
>> Connectivity : This is choose option for which router VXLAN is defined
>> Transport Zone : This is define in which boundary of DVS/N-DVS VXLAN will be configured
>> Subnet : To define Subnet of this segment
>> L2VPN : To extend it over L2VPN
>> VLAN : To encapsulate it over VLAN to support VLAN based workloads
>> Replication Mode : To choose the mode of BUM traffic handling. ( Will explain this in further blogs )
There is huge difference when compared with NSX-V and NSX-T in terms of more options on L2 related controlling options, which you will find on Segment Profile:
1. Spoof Guard
2. MAC Discovery
3. Segment Security
4. QOS
Summary
In this “NSX-T Series: Part 8 – NSX-T Logical Switching Use Cases” part, we will discussed the steps to configure logical switching for NSX-T Data Center. We went through the use cases of NSX-T Logical Segment. For further reference follow VMware Docs.Happy Learning !!!

Tualumba,
Do you have any video to refer – interesting topics but require more help to understand my friend.
Thank you.
I would recommend to follow our Youtube channel, as well as the following channel is very helpful
https://www.youtube.com/channel/UCs4WT_oht1mxGbhs-5gYKmg