Securing Internet Access Using Cisco Umbrella
The Cisco Umbrella, formerly known as OpenDNS was founded in 2006 by David Ulevitch. It fills traditional gaps in network security by blocking the outbound requests made to malicious domains
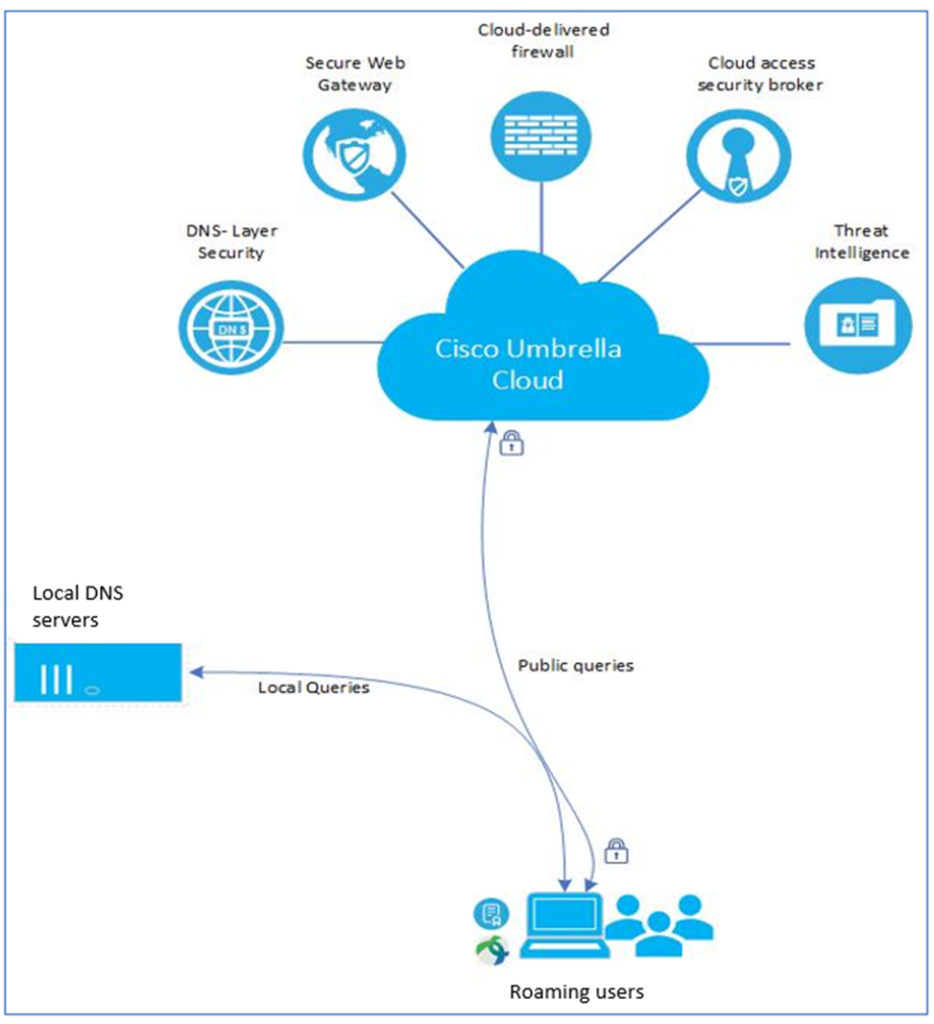
Key Use Cases
| DNS protection | Visibility into types of activities the internet-connected users and devices are requesting and the cloud services that exist in your network Enforce categorical blocking policies for acceptable use, i.e. adult content, gambling, etc |
| Remote Browser Isolation (RBI) | Isolation of web traffic between user device and browser-based threats |
| Cloud-delivered firewall(CDFW) | Provide visibility and control for traffic going to the internet Layer 3/4 firewall to log all activity and block unwanted traffic using IP, port, and protocol rules |
| CASB(Cloud access security broker) | Remove malware from cloud-based file storage applications Reports on vendor category, application name, and volume of activity Built-in content classifiers including PII, PCI and PHI |
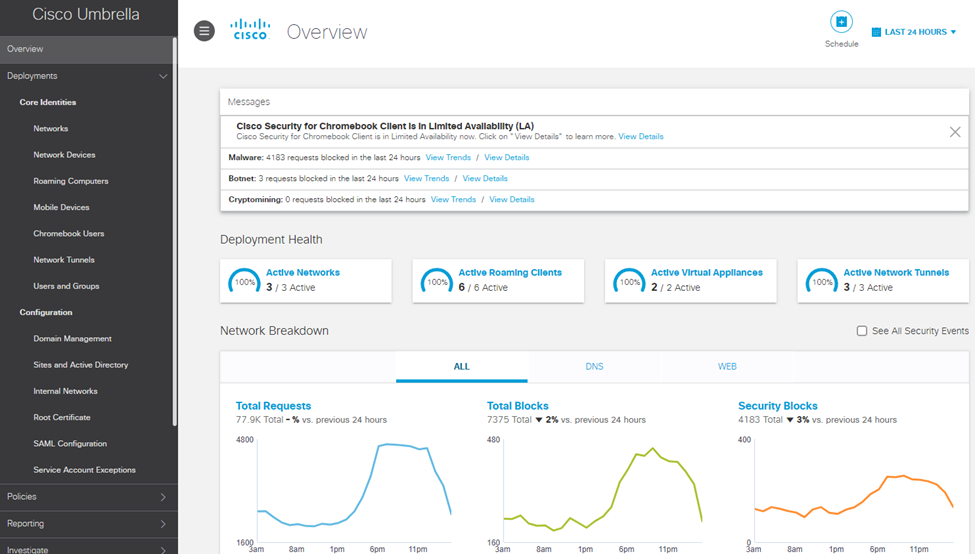
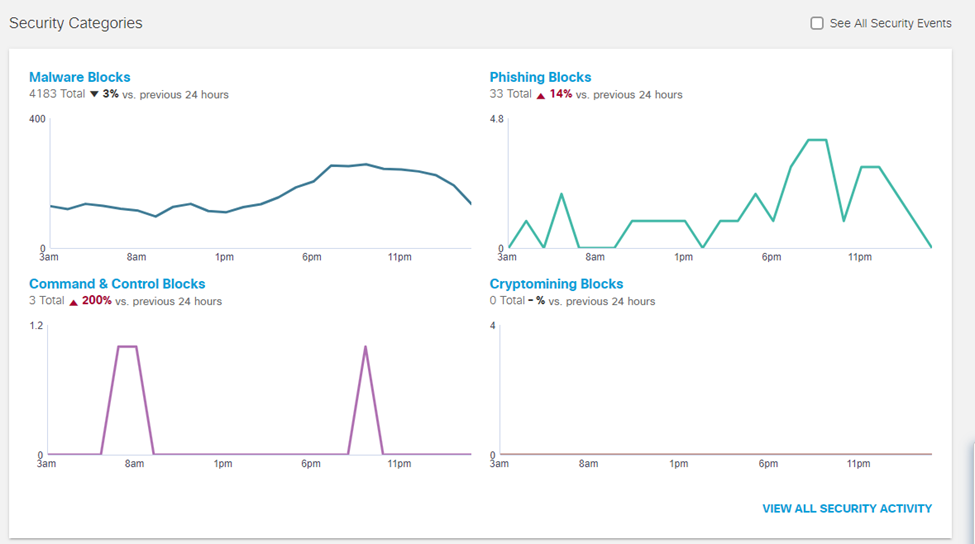
Competition and Pricing
Umbrella uses per-user licensing and also packages the features and benefits using various offerings. And, to note the direct competition to the solution is from the following key vendors
Access and Certificate Requirements
Umbrella cloud access uses standard DNS port 53/UDP and 53/TCP to communicate
| Ports and Protocol | Source/Destination |
| 53 UDP | Endpoints/208.67.222.222 Endpoints/208.67.220.220 |
| 53 TCP | Endpoints/208.67.222.222 Endpoints/208.67.220.220 |
Install the Cisco Umbrella root certificate on identified endpoints that will use the Roaming Security module. The block page uses a certificate signed by the Cisco Root CA. When the pages get access deny message, it uses the certificate to present block pages to the end user
Summary
Umbrella Global Infrastructure handles over 80 billion internet requests a day. consequently, the threat intelligence around the solution provides immense value in identifying malicious domains and associated activities. For more on security and infrastructure content please visit the Cybersecurity section