NSX-T: Exploring Distributed IDS
Using this blog “NSX-T: Exploring Distributed IDS” let’s examine distributed IDS features introduced part of NSX 3.0. and we will explore its architecture and key configuration details.
Distributed intrusion detection uses network introspection to identify malicious intrusion attempts. This results in distributed intrusion detection to protects east-west traffic and detects L4 attacks. In fact, the solution uses external signatures to identify malicious traffic across the ESXi hosts. And enables security administrators to identify security vulnerabilities in their workloads and also quarantine detected vulnerabilities.
Deployment Pre-requisite
First and foremost, the distributed intrusion detection components are installed as part of the host preparation. IDS feature support enabling it for vSphere clusters and also for standalone ESXi hosts. As a pre-requisite, Importantly with IDS, the NSX Manager requires Internet access to download signatures.
IDS Signature & Profile
In fact, the IDS signature contains data used to identify an attacker’s attempt to exploit a known vulnerability in both the operating system and applications. NSX manager downloads IDS signatures daily from a third-party repository called trust wave. These signatures are classified into one of the following severity categories.
- Critical, High, Medium and Low
The system also allows you to upload your own custom signatures and can create an IDS profile. In reality, the inclusion and exclusion of detection depend on the IDS profile signature definition
IDS Policy and Rules
An IDS policy is a collection of IDs rules, and an IDS rule contains a set of instructions that determines which traffic to be analyzed. Please note, the following items are elements of an IDS rule.
- Source and destination
- Service
- IDS profile
- Applied to ( DFW/groups)
- Action
As shown above, the DFW or to specific groups can have the IDS rules set defined. Also to note, in this release detect is the only supported action
Distributed IDS Architecture
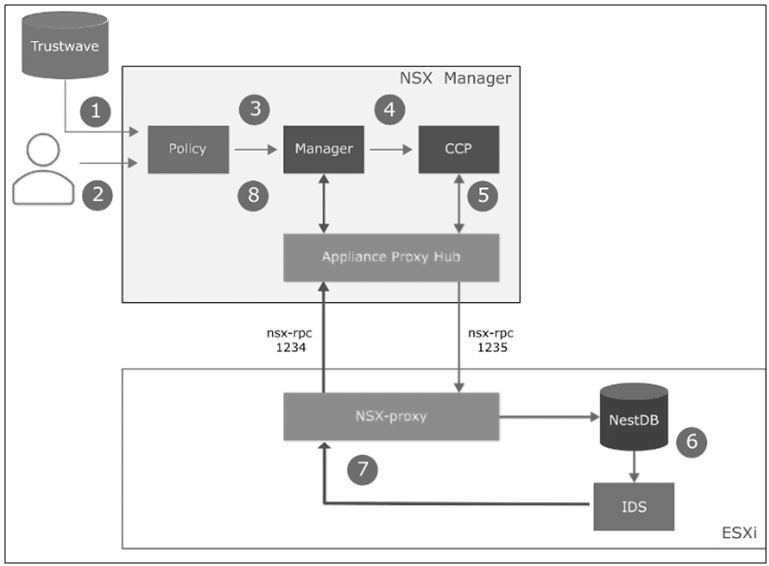
In this section we will explore the IDS workflow architecture. To begin with the NSX manager downloads the IDS signatures from trust wave. And for next step the users must configure the IDS profiles and rules. Once profiles are defined, then policy element stores the IDS configurations and passes them to the manager. NSX manager then passes the information to central control plane (CCP), and then the CCP pushes the IDS configuration to the hosts. Once the ESXi receives the configuration, it stores the signature information in NestDB then configures the data path. Finally, the ESXi host collects the traffic data and sends events to NSX manager, which parses and displays in the user interface.
Configuration and Verificaiton
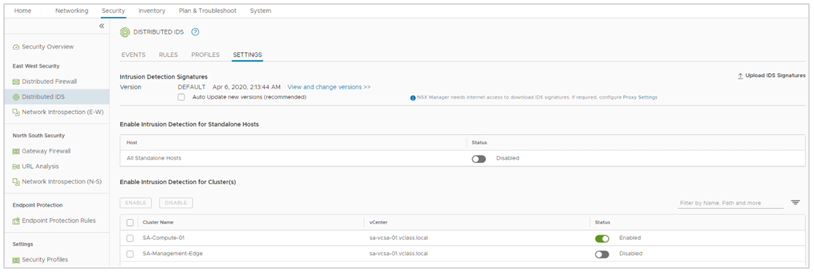
To configure distributed intrusion detection you must navigate to security – east-west security – distributed IDS settings. And enable distributed intrusion detection for standalone hosts or clusters. You can also verify the version of the IDS signatures and the last time downloaded signatures.
To create custom IDS profiles, you must navigate to Security – East West Security – Distributed IDS – Profiles in the screenshot below we see a profile with the assigned severity of critical and high
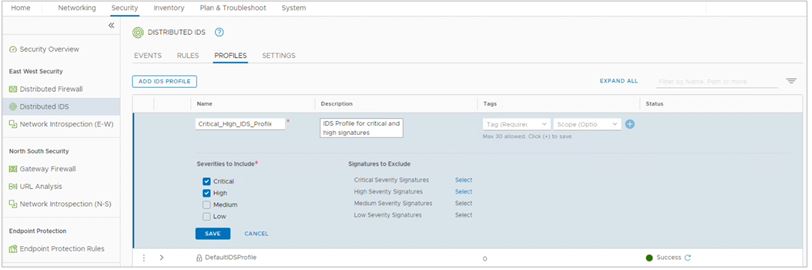
To create IDS policies and rules, you must navigate to Security – East West Security – Distributed IDS – Rules. In this screenshot, we see an IDS rule that has been configured with the Critical_High_IDS_ Profile
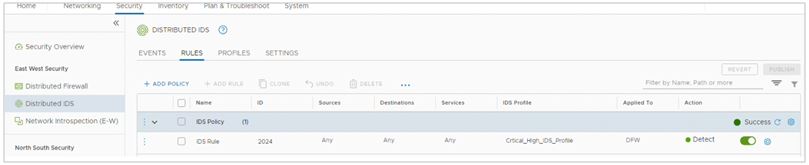
To monitor IDs events, you must navigate to Security – East West Security – Distributed IDS – Events, the IDS Events tab displays all intrusion detection attempts identified in the system.
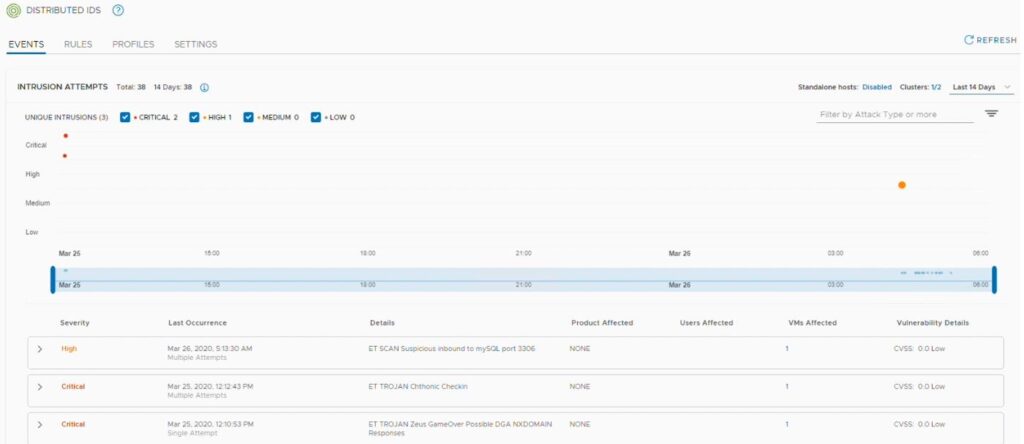
Furthermore, administrators can filter events based on their severity. Also, the freeform text is available for further filtering of events. IDS feature uses a histogram to represent the events graphically. In fact, adjusting the blue vertical lines, security administrators can specify the time period that they are interested in. Notably, each IDS event is a dot in the histogram. The size of the dot is proportional to the number of occurrences of an event. Additional information about each type of event is displayed in a tabular format. Moreover, each occurrence can be expanded to retrieve details about the intrusion attempt, including the attacker, victim, protocol, attack type, and so on.
Summary
Distributed IDS is an important function added part of the overall NSX-T distributed security landscape. I hope this blog gives you insight into its capabilities. And for more NSX-T 3.0 features and case studies, please visit VRF-Lite and NSX-T 3.0 key features and use link IDS for more information. Happy learning